Machines can also talk to each other by means of networking. Similarly, programs can become much more powerful when they have the ability to communicate with other programs via a network. In this world, you will find most systems connected in networks rather than individual. Therefore, to be a complete hacker, you must need some networking knowledge.
So now question is why hacker needs network programming ?
Network programming is an essential part of becoming a hacker.It helps in create your own hacking tools which can communicate over the internet. Let's discuss some practicle uses of network programming in real world :
* Designing malware : Suppose you are writing your own keylogger which capture keystroke(Each keyboard key press is a keystroke) and send to you. But how keylogger can send you keystorke When you physically can not access the victim's computer? It makes use of the network programming.By network programming you can send/receive data from the victim's computer.
* Developing remote exploits : If you find a vulnerability in software, say Internet explorer. As you know internet explorer is installed by default on winodws. Now you want exploit this vulnerability in your victim's system remotely. You can't exploit your victim without the network programming. With networking, you write remote exploit which exploit the vulnerability in software.
* Attacking network application like SMTP, FTP : There are many networking applications like Apache http server, FTP(File transfer protocol), ssh. Now suppose you attacking ssh(Secure shell, port no.22 ) for username and password through brute force attack. To communicate with ssh for username and password you need to network programming in your brute-force program.
Learn networking :
Knowing as much as you can about how a network operates, including basics such as what an IP address, port, protocol, and the thousands of other networking definitions, can be yet another vital thing to learn about.
OSI Network Layer Model :
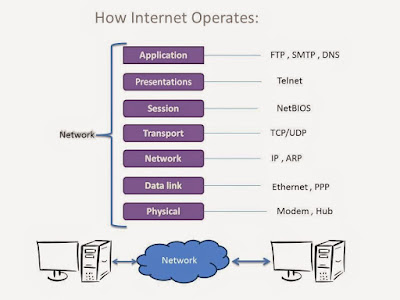
Before we start learn about network, let's first we discuss about network architecture. ISO designed the standardized architecture of networks known as OSI (Open Systems Interconnection). The OSI architecture is a layered model of an ideal network. The OSI model provides standards that allow hardware, such as routers and firewalls, to focus on one particular aspect of communication that applies to them and ignore others. The OSI model is broken down into conceptual layers of communication.
Physical Layer: This is the 1st layer of OSI model. This layer is composed of hardware. The network cables and other network hardware devices lie in this layer.
Data Link Layer: This is the 2nd layer of OSI model. The Ethernet protocol works in this layer. The devices in this layer are addressed using their hardware address also known as MAC (Media Access Control) address.
Network Layer: This is the 3rd layer of OSI model. The networks are broken into logical segments into this layer. The networked systems are identified with IP (internet protocol) addresses into this layer.
Transport Layer: This is the most important layer. The transport layer is the 4th layer of OSI model. The TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) work in this layer.
Session Layer: Te session layer as name suggests keeps track of all connections (sessions). This layer keeps track of the data provided by the upper layers and sends them to their respective lower layer circuits.
Presentation Layer: This layer is most important from security point of view. The encryption if applied can be applied here on the data.
Application Layer: This layer is the main application, i.e. the program, which may or may not be interacting with the user.
When data is communicated through these protocol layers, it’s sent in small pieces called packets. Each packet contains implementations of these protocol layers. Starting from the application layer, the packet wraps the presentation layer around that data, which wraps the session layer, which wraps the transport layer, and so forth. This process is called encapsulation. Each wrapped layer contains a header and a body. The header contains the protocol information needed for that layer, while the body contains the data for that layer. The body of one layer contains the entire package of previously encapsulated layers, like the skin of an onion or the functional contexts found on a program’s stack.
So now question is why hacker needs network programming ?
Network programming is an essential part of becoming a hacker.It helps in create your own hacking tools which can communicate over the internet. Let's discuss some practicle uses of network programming in real world :
* Designing malware : Suppose you are writing your own keylogger which capture keystroke(Each keyboard key press is a keystroke) and send to you. But how keylogger can send you keystorke When you physically can not access the victim's computer? It makes use of the network programming.By network programming you can send/receive data from the victim's computer.
* Developing remote exploits : If you find a vulnerability in software, say Internet explorer. As you know internet explorer is installed by default on winodws. Now you want exploit this vulnerability in your victim's system remotely. You can't exploit your victim without the network programming. With networking, you write remote exploit which exploit the vulnerability in software.
* Attacking network application like SMTP, FTP : There are many networking applications like Apache http server, FTP(File transfer protocol), ssh. Now suppose you attacking ssh(Secure shell, port no.22 ) for username and password through brute force attack. To communicate with ssh for username and password you need to network programming in your brute-force program.
Learn networking :
Knowing as much as you can about how a network operates, including basics such as what an IP address, port, protocol, and the thousands of other networking definitions, can be yet another vital thing to learn about.
OSI Network Layer Model :
Before we start learn about network, let's first we discuss about network architecture. ISO designed the standardized architecture of networks known as OSI (Open Systems Interconnection). The OSI architecture is a layered model of an ideal network. The OSI model provides standards that allow hardware, such as routers and firewalls, to focus on one particular aspect of communication that applies to them and ignore others. The OSI model is broken down into conceptual layers of communication.
Physical Layer: This is the 1st layer of OSI model. This layer is composed of hardware. The network cables and other network hardware devices lie in this layer.
Data Link Layer: This is the 2nd layer of OSI model. The Ethernet protocol works in this layer. The devices in this layer are addressed using their hardware address also known as MAC (Media Access Control) address.
Network Layer: This is the 3rd layer of OSI model. The networks are broken into logical segments into this layer. The networked systems are identified with IP (internet protocol) addresses into this layer.
Transport Layer: This is the most important layer. The transport layer is the 4th layer of OSI model. The TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) work in this layer.
Session Layer: Te session layer as name suggests keeps track of all connections (sessions). This layer keeps track of the data provided by the upper layers and sends them to their respective lower layer circuits.
Presentation Layer: This layer is most important from security point of view. The encryption if applied can be applied here on the data.
Application Layer: This layer is the main application, i.e. the program, which may or may not be interacting with the user.
When data is communicated through these protocol layers, it’s sent in small pieces called packets. Each packet contains implementations of these protocol layers. Starting from the application layer, the packet wraps the presentation layer around that data, which wraps the session layer, which wraps the transport layer, and so forth. This process is called encapsulation. Each wrapped layer contains a header and a body. The header contains the protocol information needed for that layer, while the body contains the data for that layer. The body of one layer contains the entire package of previously encapsulated layers, like the skin of an onion or the functional contexts found on a program’s stack.
where do i start? got some tutorials?
ReplyDeleteWhat do you want to start? As far as i understand you want to learn network programming in hacker way ? Please correct me if i am wrong ?
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteI can feel the passion you have for low level stuf bro, that I share as well... good work. keep going. and thank you for sharing.
ReplyDeleteThanks for your valuable feedback !
DeleteYour blog is very helpful to training seekers like me. CEH Training in India is a qualification obtained by assessing the security of computer. Good work.
ReplyDeleteFRESH FULLZ AVAILABLE
ReplyDeleteSSN+DOB
SSN+DOB+DL
HIGH CREDIT CORES
DUMPS WITH PIN (TRACK 101 & 202)
I C Q = 752822040
Tele-Gram = @killhacks
Hac-king, Spa-mming, Car-ding, Scr-pting
TOOLS AVAILABLE
WITH COMPLETE TUTORIALS GUIDE & EBOOKS
C-PANELS
MAILERS
SMS-BOOMBER
KEY-LOGGERS
VIR-USES
kALi LiNUX COMPLETE PACKAGE
DAR-K W-EB cOMPLLETE cOURSE
Contact:
I C Q = 752822040
Tele-Gram = @killhacks
Good day everyone, My partner and I are a few of the lucky ones who were able to recover their stolen bitcoins from online scammers with the help of Spyweb Cyber. A few months back, we invested our retirement money into a cryptocurrency investment platform BTCglobal and were hoping to make huge returns from our investment, after some weeks when it was time to withdraw our money, they requested we pay 20% or lose everything. We reported it to the authorities and they told us it was a scam and our money is lost forever. We were depressed not until a friend of ours told us about Spyweb Cyber, a reputable cryptocurrency recovery company that can help us recover everything. We contacted them and provided the information they needed, and in the space of 48 hours, our funds were recovered. We are truly grateful that such a company as Spyweb exists. This is their contact information if you need their help.
ReplyDeleteSpyweb@cyberdude(.)com & Contact@spyweb(.)tech