Windows NT has been around a shorter time period than UNIX, so it is
natural that UNIX is a more mature operating system. However, Windows NT
is user-interface that's why about 90% computer uses windows.For those
of us who write code, we know that there is a direct correlation between
the features of a piece of software and the number of lines of code.
The more features you add, the more code is needed to support these
features. There is also a correlation between the amount of code and the
number of bugs that are in the code. As the size of the code increases,
the chance for unforeseen issues to appear in the code also
increases.Based on the time factor, most code (and NT is no exception)
is developed so quickly that error checking is either ignored or done
poorly. By doing this, the developers are saying that they trust anyone
who will use the software to do the right thing, therefore believing
that they are secure.If proper error checking were performed on all
data, a lot of the security vulnerabilities would go away.
Windows NT Fundamentals:
we will look at some of the core concepts of NT that will help you understand how attackers break in.Remember the purpose of this tutorial is not to show an attacker how to break into systems.You can use this knowledge to secure your systems and minimize the damage that an attacker can cause.
The following topics will cover in this tutorial:
1. NT Architecture
2.Windows Security
3. Registry
4.Services running
5.Auditing
1. NT Architecture:The key about NT is that there are two basic modes: User mode, has much more restricted access and must request services from the kernel in many instances to complete certain tasks, such as accessing hardware resources, authenticating users, and modifying the system. kernel mode,has effectively unrestricted access to system resources.
Attacking the Kernel : If someone can insert code of their choosing into kernel mode, the system is utterly compromised.As you might imagine, Windows provides substantial barriers to running arbitrary code in kernel mode, and it is generally quite difficult for low-privileged entities to do so.
Two primary classes of kernel mode compromises can occur:
1.Physical attacks against kernel-resident device drivers that parse raw input, such as from network connections or inserted media.
2.Logical attacks against critical operating system structures that provide access to kernel mode. These structures include certain protected kernel images (such as ntoskrnl.exe, hal.dll, and ndis.sys), the Global Descriptor Table (GDT) and the Interrupt Descriptor Table (IDT), the System Service Descriptor Table (SSDT), certain critical processor–model-specific registers (MSRs).
The hardware abstraction layer (HAL) is the piece that directly interacts with the hardware. This allows NT to run on different hardware platforms like Intel and DEC ALPHA. If the system weren’t designed in this fashion, the entire system would have to be rewritten for new hardware.
Kernel gets its configuration from the Registry.This is one of the reasons why the Registry is so critical, because if it gets corrupted, the Kernel cannot load, which means the operating system cannot run.
One question you might be asking is this: If programmers are supposed to operate only at the user mode, doesn’t that limit the functionality and power of the programs, because there are cases where someone would want to access the Kernel? In these cases, there are APIs, or application programming interfaces. APIs are gateways that programmers use to allow them to make calls to the subsystem, which in turn makes calls to the Kernel.
Attacking user mode:User mode code serves effectively as the door and window into resources and data on the system. Obviously, this code must be able to access resources and data, or the operating system would offer a pretty poor user experience. Thus, if you can authenticate to Windows as an authorized user, you will have access to all the resources and data relevant to that user. Furthermore, if you are lucky enough to authenticate as an administrative user, you will likely have access to the resources and data for all the users on the system.
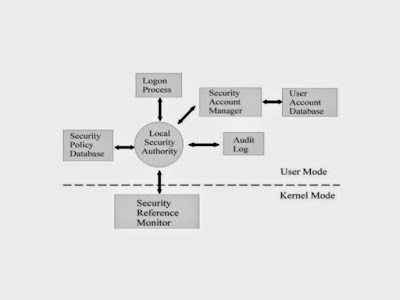
2. Windows Security:There are three components of Windows Security:
LSA (Local Security Authority)
SAM (Security Account Manager)
SRM (Security Reference Monitor)
LSA (Local Security Authority):LSA is the Central Part of NT Security. It is also known as Security Subsystem. The Local Security Authority or LSA is a key component of the logon process in both Windows NT and Windows 2000. In Windows 2000, the LSA is responsible for validating users for both local and remote logons. The LSA also maintains the local security policy.During the local logon to a machine, a person enters his name and password to the logon dialog. This information is passed to the LSA, which then calls the appropriate authentication package. The password is sent in a nonreversible secret key format using a one-way hash function. The LSA then queries the SAM database for the User’s account information. If the key provided matches the one in the SAM, the SAM returns the users SID and the SIDs of any groups the user belongs to. The LSA then uses these SIDs to generate the security access token.
SAM (Security Account Manager): The Security Accounts Manager is a database in the Windows operating system (OS) that contains user names and passwords. SAM is part of the registry and can be found on the hard disk.This service is responsible for making the connection to the SAM database (Contains available user-accounts and groups). The SAM database can either be placed in the local registry or in the Active Directory (If available). When the service has made the connection it announces to the system that the SAM-database is available, so other services can start accessing the SAM-database.In the SAM, each user account can be assigned a Windows password which is in encrypted form. If someone attempts to log on to the system and the user name and associated passwords match an entry in the SAM, a sequence of events takes place ultimately allowing that person access to the system. If the user name or passwords do not properly match any entry in the SAM, an error message is returned requesting that the information be entered again.When you make a New User Account with a Password, it gets stored in the SAM File.
SRM (Security Reference Monitor):The Security Reference Monitor is a security architecture component that is used to control user requests to access objects in the system. The SRM enforces the access validation and audit generation. Windows NT forbids the direct access to objects. Any access to an object must first be validated by the SRM. For example, if a user wants to access a specific file the SRM will be used to validate the request. The Security Reference Monitor enforces access validation and audit generation policy.
3. Registry: The Registry is a database used to store settings and options for Microsoft windows. It contains information and settings for all the hardware, software, users, and preferences of the PC. Whenever a user makes changes to a Control Panel settings, or File Associations, System Policies, or installed software, the changes are reflected and stored in the Registry.
It is critical to the security of an NT system because If an attacker goes in and modifies some values in the
Registry, the operating system can stop working. The only way to fix it is to reinstall the operating system or boot with an alternate kernel or from a different device and restore a backup of the Registry.
The Structure of the Registry :
There are five main hives, each containing a specific portion of the information stored of the Registry :
HKEY_CLASSES_ROOT // it contain file type associations.
HKEY_CURRENT_USER // it contains preferences and settings of the currently logged on user.
HKEY_LOCAL_MACHINE // it contains specific information about the type of hardware, software // and security info.
HKEY_USERS // It contains data from every user in the SAM.
HKEY_CURRENT_CONFIG // it contains information gathered at runtime; information stored in this key
// is not permanently stored on disk,but rather regenerated at boot time.
How to change a setting in the Windows Registry: first Make sure that you have a backup of the Registry before attempting to make any changes to it.
Go to the Start Menu, type Regedit, and hit Enter. If a User Account Control security question shows up, answer with Yes.
On the left side of the Registry Editor screen you can browse all the different hives and keys of the Windows Registry. On the right side,you will see their current corresponding values.
Now browse to this key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer
Double-click the link value on the right side. Mark the number 16 by selecting it with the mouse, and type 00 (two zeros) to replace the 16 with 00. The link value now reads 00. Click OK and close the Registry Editor.
Now reboot your computer and you have done.
Importing and Exporting Registry Settings:
Exporting a Registry key is necessary if you want to copy a specific setting or the configuration of an application (located in HKEY_CURRENT_USER\Software and HKEY_LOCAL_MACHINE\Software) to another computer.
To export a Windows Registry key, right-click it and select Export. Give it a name -- for example, CopyTo. The Registry Editor will create a file called CopyTo.reg, a text file that can be viewed or edited with a text editor like Notepad or GetDiz.
To import the content of the exported .reg file to the Registry on another Windows computer, just double-click on it. You will be asked if you want to import it to the Windows Registry.
Remember a careless change in window registry may cause serious damage. If you are not master in window registry then never change any value in registry.You will not become an expert in the Registry overnight, but it is important that you understand the basics of how it works.
4. Services running:To see what services are running, select Start, Settings, Control Panel,and click on the Services icon.
You can scroll down this list and see what services are running. When looking, it is important to note that even if a service is not started, it can still be a vulnerability. If the service is not installed at all and an attacker wants to exploit the service, he first must install the service on the machine, which is a lot of work. On the other hand, if the service is installed but not started, it is easy for an attacker to start it up—and all of a sudden your system becomes unsecure.All of a sudden, if three new services are running, it could be a good indication that a system has been compromised. It could also mean that an attacker loaded software on the system that required these services to be running, without the administrator’s knowledge.
5. AUDITING :
Event Viewer in Windows: Event logs are local files recording all the 'happenings' on the system and it includes accessing, deleting, adding a file or an application, modifying the system's date, shuting down the system, changing the system configuration, etc.Events that are related to system or data security are called security events and its log file is called Security logs.
Get started:
Start the Event Viewer by typing event viewer into the Start Menu search box. You can also go to Control Panel -> System and Security -> Administrative Tools -> Event Viewer.
More in detail:Event_Viewer
Reference:Hackers Beware: The Ultimate Guide to Network Security
If you like this post or have any question, please feel free to comment !
Windows NT Fundamentals:
we will look at some of the core concepts of NT that will help you understand how attackers break in.Remember the purpose of this tutorial is not to show an attacker how to break into systems.You can use this knowledge to secure your systems and minimize the damage that an attacker can cause.
The following topics will cover in this tutorial:
1. NT Architecture
2.Windows Security
3. Registry
4.Services running
5.Auditing
1. NT Architecture:The key about NT is that there are two basic modes: User mode, has much more restricted access and must request services from the kernel in many instances to complete certain tasks, such as accessing hardware resources, authenticating users, and modifying the system. kernel mode,has effectively unrestricted access to system resources.
Attacking the Kernel : If someone can insert code of their choosing into kernel mode, the system is utterly compromised.As you might imagine, Windows provides substantial barriers to running arbitrary code in kernel mode, and it is generally quite difficult for low-privileged entities to do so.
Two primary classes of kernel mode compromises can occur:
1.Physical attacks against kernel-resident device drivers that parse raw input, such as from network connections or inserted media.
2.Logical attacks against critical operating system structures that provide access to kernel mode. These structures include certain protected kernel images (such as ntoskrnl.exe, hal.dll, and ndis.sys), the Global Descriptor Table (GDT) and the Interrupt Descriptor Table (IDT), the System Service Descriptor Table (SSDT), certain critical processor–model-specific registers (MSRs).
The hardware abstraction layer (HAL) is the piece that directly interacts with the hardware. This allows NT to run on different hardware platforms like Intel and DEC ALPHA. If the system weren’t designed in this fashion, the entire system would have to be rewritten for new hardware.
Kernel gets its configuration from the Registry.This is one of the reasons why the Registry is so critical, because if it gets corrupted, the Kernel cannot load, which means the operating system cannot run.
One question you might be asking is this: If programmers are supposed to operate only at the user mode, doesn’t that limit the functionality and power of the programs, because there are cases where someone would want to access the Kernel? In these cases, there are APIs, or application programming interfaces. APIs are gateways that programmers use to allow them to make calls to the subsystem, which in turn makes calls to the Kernel.
Attacking user mode:User mode code serves effectively as the door and window into resources and data on the system. Obviously, this code must be able to access resources and data, or the operating system would offer a pretty poor user experience. Thus, if you can authenticate to Windows as an authorized user, you will have access to all the resources and data relevant to that user. Furthermore, if you are lucky enough to authenticate as an administrative user, you will likely have access to the resources and data for all the users on the system.
2. Windows Security:There are three components of Windows Security:
LSA (Local Security Authority)
SAM (Security Account Manager)
SRM (Security Reference Monitor)
LSA (Local Security Authority):LSA is the Central Part of NT Security. It is also known as Security Subsystem. The Local Security Authority or LSA is a key component of the logon process in both Windows NT and Windows 2000. In Windows 2000, the LSA is responsible for validating users for both local and remote logons. The LSA also maintains the local security policy.During the local logon to a machine, a person enters his name and password to the logon dialog. This information is passed to the LSA, which then calls the appropriate authentication package. The password is sent in a nonreversible secret key format using a one-way hash function. The LSA then queries the SAM database for the User’s account information. If the key provided matches the one in the SAM, the SAM returns the users SID and the SIDs of any groups the user belongs to. The LSA then uses these SIDs to generate the security access token.
SAM (Security Account Manager): The Security Accounts Manager is a database in the Windows operating system (OS) that contains user names and passwords. SAM is part of the registry and can be found on the hard disk.This service is responsible for making the connection to the SAM database (Contains available user-accounts and groups). The SAM database can either be placed in the local registry or in the Active Directory (If available). When the service has made the connection it announces to the system that the SAM-database is available, so other services can start accessing the SAM-database.In the SAM, each user account can be assigned a Windows password which is in encrypted form. If someone attempts to log on to the system and the user name and associated passwords match an entry in the SAM, a sequence of events takes place ultimately allowing that person access to the system. If the user name or passwords do not properly match any entry in the SAM, an error message is returned requesting that the information be entered again.When you make a New User Account with a Password, it gets stored in the SAM File.
SRM (Security Reference Monitor):The Security Reference Monitor is a security architecture component that is used to control user requests to access objects in the system. The SRM enforces the access validation and audit generation. Windows NT forbids the direct access to objects. Any access to an object must first be validated by the SRM. For example, if a user wants to access a specific file the SRM will be used to validate the request. The Security Reference Monitor enforces access validation and audit generation policy.
3. Registry: The Registry is a database used to store settings and options for Microsoft windows. It contains information and settings for all the hardware, software, users, and preferences of the PC. Whenever a user makes changes to a Control Panel settings, or File Associations, System Policies, or installed software, the changes are reflected and stored in the Registry.
It is critical to the security of an NT system because If an attacker goes in and modifies some values in the
Registry, the operating system can stop working. The only way to fix it is to reinstall the operating system or boot with an alternate kernel or from a different device and restore a backup of the Registry.
The Structure of the Registry :
There are five main hives, each containing a specific portion of the information stored of the Registry :
HKEY_CLASSES_ROOT // it contain file type associations.
HKEY_CURRENT_USER // it contains preferences and settings of the currently logged on user.
HKEY_LOCAL_MACHINE // it contains specific information about the type of hardware, software // and security info.
HKEY_USERS // It contains data from every user in the SAM.
HKEY_CURRENT_CONFIG // it contains information gathered at runtime; information stored in this key
// is not permanently stored on disk,but rather regenerated at boot time.
How to change a setting in the Windows Registry: first Make sure that you have a backup of the Registry before attempting to make any changes to it.
Go to the Start Menu, type Regedit, and hit Enter. If a User Account Control security question shows up, answer with Yes.
On the left side of the Registry Editor screen you can browse all the different hives and keys of the Windows Registry. On the right side,you will see their current corresponding values.
Now browse to this key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer
Double-click the link value on the right side. Mark the number 16 by selecting it with the mouse, and type 00 (two zeros) to replace the 16 with 00. The link value now reads 00. Click OK and close the Registry Editor.
Now reboot your computer and you have done.
Importing and Exporting Registry Settings:
Exporting a Registry key is necessary if you want to copy a specific setting or the configuration of an application (located in HKEY_CURRENT_USER\Software and HKEY_LOCAL_MACHINE\Software) to another computer.
To export a Windows Registry key, right-click it and select Export. Give it a name -- for example, CopyTo. The Registry Editor will create a file called CopyTo.reg, a text file that can be viewed or edited with a text editor like Notepad or GetDiz.
To import the content of the exported .reg file to the Registry on another Windows computer, just double-click on it. You will be asked if you want to import it to the Windows Registry.
Remember a careless change in window registry may cause serious damage. If you are not master in window registry then never change any value in registry.You will not become an expert in the Registry overnight, but it is important that you understand the basics of how it works.
4. Services running:To see what services are running, select Start, Settings, Control Panel,and click on the Services icon.
You can scroll down this list and see what services are running. When looking, it is important to note that even if a service is not started, it can still be a vulnerability. If the service is not installed at all and an attacker wants to exploit the service, he first must install the service on the machine, which is a lot of work. On the other hand, if the service is installed but not started, it is easy for an attacker to start it up—and all of a sudden your system becomes unsecure.All of a sudden, if three new services are running, it could be a good indication that a system has been compromised. It could also mean that an attacker loaded software on the system that required these services to be running, without the administrator’s knowledge.
5. AUDITING :
Event Viewer in Windows: Event logs are local files recording all the 'happenings' on the system and it includes accessing, deleting, adding a file or an application, modifying the system's date, shuting down the system, changing the system configuration, etc.Events that are related to system or data security are called security events and its log file is called Security logs.
Get started:
Start the Event Viewer by typing event viewer into the Start Menu search box. You can also go to Control Panel -> System and Security -> Administrative Tools -> Event Viewer.
More in detail:Event_Viewer
Reference:Hackers Beware: The Ultimate Guide to Network Security
If you like this post or have any question, please feel free to comment !

Process of reverse engineering Denver, Colorado saves time and overall costs of the project since all the design tests are done way before manufacturing; there are very few chances of ECO or reworks. You can hire people to do the job. Make sure you get the professional ones.
ReplyDeleteThanks for Sharing a Very Informative Post & I read Your Article & I must say that is very helpful post for us.
ReplyDeletePoint cloud to 3D Model Reading
Scan to BIM in California
3d Laser Scanning Services in Georgia
Reverse Engineering Services in California