An array allows us to declare a collections of variables that referenced by a common name.
Suppose you have to write a program which stores marks of 50 students.
In normal way, you declare 50 variables which store the value of 50 student's marks. So instead of creating individually variables, this can be done by using Arrays. Instead of declaring individual variables, such as marks0, marks1, ..., and marks49, you declare one array variable such as "marks" and use marks[0], marks[1], and ..., marks[49] to represent individual variables. A specific element in an array is accessed by an index.
The concept of array is very-very important for hackers. Most of exploits like stack overflow are exist because of improper handling of arrays. A programmer knows how to use array to store data but a hacker knows how to use arrays perfectly.Stack-based overflows occur when a static-sized local buffer is overflowed by attempting to store more data within the buffer than its fixed size allows. And around 70% exploits are Stack-based overflows. We will discuss later about buffer overflow.
As arrays are Variables, so to use Arrays, they must be declared before they can be used. Arrays are of two types:
One-dimensional arrays
Multidimensional arrays(Two or more)
To declare an array in C, a programmer specifies the type of the elements and the number of elements required by an array as follows:
data_type arrayName [Size];
For example:
int marks[49];
this is declaration of one-dimensional array.
Initialization of one-dimensional array:
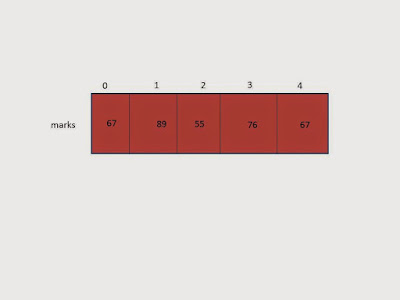
int marks[5]={67,89,55,76,67};
pictorial representation of the array we discussed above:
Accessing Array Elements:
An element is accessed by indexing the array name. This is done by placing the index of the element within square brackets after the name of the array.
Let's see:
int result = marks[4];
The above statement will take 4th element from the array and assign the value to result variable.
Passing Arrays as Function Arguments :
When an array is used as an argument to a function, only the address of the array gets passed, not a copy of entire array. There are 3 ways to declare a parameter that is to receive an array pointer.
First Way: The receiving parameter of the array may itself be declared as an array, as :
int main()
{
int marks[49];
.
.//Function code like initialize array
.
.
result(marks);
}
void result(int m[49]) //receiving parameter has been declared as array with its size.
{
//Function code
}
Second Way: The receiving parameter may be declared as an unsized array, as:
int main()
{
int marks[49];
.
.//Function code like initialize array
.
.
result(marks);
}
void result(int m[]) //receiving parameter has been declared as array without size.
{
//Function code
}
Third way: The receiving parameter can be declared as a pointer, as:
int main()
{
int marks[49];
.
.//Function code like intilize array
.
.
result(marks);
}
void result(int *m) //receiving parameter has benn declared as pointer of same base type.
{
//Function code
}
String: The string in C programming language is actually a one-dimensional array of characters which is terminated by a null character '\0':
char mgs[6] = {'H', 'e', 'l', 'l', 'o', '\0'};
An even easier way of initializing is a string is:
char mgs[6] = “hello”;
Note the use of double quotes here as opposed to the single quotes in the previous example. The double quotes tells the compiler “hello” is a string and a null will automatically be appended to the end.
The null terminator is very significant to some hackers.
consider this code:
char marks[50] = “marks”;
printf(“%s”, marks);
This code will print:
marks
It doesn’t print the entire 50 characters of marks[50]. C will read a string until it reaches the null. If it reaches null before the end of the array, that’s where it stops. Nothing beyond there is read.
The problem occurs when a 0 is found in the code. When the computer comes across a 0, it is interpreted as a null, and the read operation ends.This is very common problem in writing shellcodes. Suppose your shell code were injected into a character buffer overflow, a 0 is occurred at fifth lines, then only the first four lines would execute only. Because The fifth line has a zero, which is interpreted as “end of string”.
Now here the question may arise is what is buffer overflow or character buffer overflow ? I think now it is the perfect time to introduce topic of buffer overflow.
char name[10];
printf(“Please enter your name:\n”);
scanf(“%s”, name);
printf(“Your name is: %s”, name);
Here we declare an char array of size 10. Then we take input(suppose username) from user and then print it out.
A user may or may not supplied a username of length of less than or equal to 10.But what if user supplied more than 10 characters ?
The computer will take this input(more than 10 characters) and store it in memory starting at the address pointed to by ‘name’. The problem is that the code has only put aside 10 bytes for name. suppose You entered 25 characters, Then the remaining 15 characters write over whatever is the in space after the space allocated to ‘name’.
The extra 15 characters would overwrite the return instruction pointer, in essence creating a new value in the EIP register.You can poison the return value while it’s on the stack. In this case, you could inject a new instruction pointer and take control of the execution of the program.
Vulnerable Buffers :
In C language, strings, or buffers, are represented by a pointer to the address of their first byte, and we consider we have reached the end of the buffer when we see a NULL byte. This means that there is no way to set precisely the amount of memory reserved for a buffer, it all depends on the number of characters.
the size problem makes restricting the memory allocated to a buffer, to prevent any overflow, quite difficult. That is why some trouble may be observed, for instance when strcpy is used without care,which allows a user to copy a buffer into another smaller one !
We will discuss more on overflow in upcoming Tutorials.
If you like this post or have any question, please feel free to comment !
Suppose you have to write a program which stores marks of 50 students.
In normal way, you declare 50 variables which store the value of 50 student's marks. So instead of creating individually variables, this can be done by using Arrays. Instead of declaring individual variables, such as marks0, marks1, ..., and marks49, you declare one array variable such as "marks" and use marks[0], marks[1], and ..., marks[49] to represent individual variables. A specific element in an array is accessed by an index.
The concept of array is very-very important for hackers. Most of exploits like stack overflow are exist because of improper handling of arrays. A programmer knows how to use array to store data but a hacker knows how to use arrays perfectly.Stack-based overflows occur when a static-sized local buffer is overflowed by attempting to store more data within the buffer than its fixed size allows. And around 70% exploits are Stack-based overflows. We will discuss later about buffer overflow.
As arrays are Variables, so to use Arrays, they must be declared before they can be used. Arrays are of two types:
One-dimensional arrays
Multidimensional arrays(Two or more)
To declare an array in C, a programmer specifies the type of the elements and the number of elements required by an array as follows:
data_type arrayName [Size];
For example:
int marks[49];
this is declaration of one-dimensional array.
Initialization of one-dimensional array:
int marks[5]={67,89,55,76,67};
pictorial representation of the array we discussed above:
Accessing Array Elements:
An element is accessed by indexing the array name. This is done by placing the index of the element within square brackets after the name of the array.
Let's see:
int result = marks[4];
The above statement will take 4th element from the array and assign the value to result variable.
Passing Arrays as Function Arguments :
When an array is used as an argument to a function, only the address of the array gets passed, not a copy of entire array. There are 3 ways to declare a parameter that is to receive an array pointer.
First Way: The receiving parameter of the array may itself be declared as an array, as :
int main()
{
int marks[49];
.
.//Function code like initialize array
.
.
result(marks);
}
void result(int m[49]) //receiving parameter has been declared as array with its size.
{
//Function code
}
Second Way: The receiving parameter may be declared as an unsized array, as:
int main()
{
int marks[49];
.
.//Function code like initialize array
.
.
result(marks);
}
void result(int m[]) //receiving parameter has been declared as array without size.
{
//Function code
}
Third way: The receiving parameter can be declared as a pointer, as:
int main()
{
int marks[49];
.
.//Function code like intilize array
.
.
result(marks);
}
void result(int *m) //receiving parameter has benn declared as pointer of same base type.
{
//Function code
}
String: The string in C programming language is actually a one-dimensional array of characters which is terminated by a null character '\0':
char mgs[6] = {'H', 'e', 'l', 'l', 'o', '\0'};
An even easier way of initializing is a string is:
char mgs[6] = “hello”;
Note the use of double quotes here as opposed to the single quotes in the previous example. The double quotes tells the compiler “hello” is a string and a null will automatically be appended to the end.
The null terminator is very significant to some hackers.
consider this code:
char marks[50] = “marks”;
printf(“%s”, marks);
This code will print:
marks
It doesn’t print the entire 50 characters of marks[50]. C will read a string until it reaches the null. If it reaches null before the end of the array, that’s where it stops. Nothing beyond there is read.
The problem occurs when a 0 is found in the code. When the computer comes across a 0, it is interpreted as a null, and the read operation ends.This is very common problem in writing shellcodes. Suppose your shell code were injected into a character buffer overflow, a 0 is occurred at fifth lines, then only the first four lines would execute only. Because The fifth line has a zero, which is interpreted as “end of string”.
Now here the question may arise is what is buffer overflow or character buffer overflow ? I think now it is the perfect time to introduce topic of buffer overflow.
char name[10];
printf(“Please enter your name:\n”);
scanf(“%s”, name);
printf(“Your name is: %s”, name);
Here we declare an char array of size 10. Then we take input(suppose username) from user and then print it out.
A user may or may not supplied a username of length of less than or equal to 10.But what if user supplied more than 10 characters ?
The computer will take this input(more than 10 characters) and store it in memory starting at the address pointed to by ‘name’. The problem is that the code has only put aside 10 bytes for name. suppose You entered 25 characters, Then the remaining 15 characters write over whatever is the in space after the space allocated to ‘name’.
The extra 15 characters would overwrite the return instruction pointer, in essence creating a new value in the EIP register.You can poison the return value while it’s on the stack. In this case, you could inject a new instruction pointer and take control of the execution of the program.
Vulnerable Buffers :
In C language, strings, or buffers, are represented by a pointer to the address of their first byte, and we consider we have reached the end of the buffer when we see a NULL byte. This means that there is no way to set precisely the amount of memory reserved for a buffer, it all depends on the number of characters.
the size problem makes restricting the memory allocated to a buffer, to prevent any overflow, quite difficult. That is why some trouble may be observed, for instance when strcpy is used without care,which allows a user to copy a buffer into another smaller one !
We will discuss more on overflow in upcoming Tutorials.
If you like this post or have any question, please feel free to comment !
love.
ReplyDelete