What is the difference between hacker and programmer?
A programmer is one who only concerned with source code.A hacker is someone who is curious about how something(like computer) works.A hacker realizes that the compiled program is what actually gets executed out in the real world.The hacker wants to know the ins and outs, nuts and bolts of the entire thing.If you really want to be a hacker, you must want to understand the working guts of a computer.With a better understanding of how the CPU operates, a hacker can manipulate the programs that run on it.
A programmer writes the code,compiled it into an executable binary for the low level(x86 assumed) architecture. But what does this executable binary look like? It does not make sense to programmers but a hacker realizes that the compiled program is what actually gets executed out in the real world.With a better understanding of how the CPU operates, a hacker can manipulate the programs that run on it.
The CPU is is the heart of the system. it designed to do a couple of things:
Fetch an instruction from memory.
Execute the instruction.
There are two kind of processor architecture:
Big Endian
Little Endian
Little and big endian are two ways of storing multibyte data-types ( int, float, etc).Big endian stores data in such a way that most significant byte is stored at lower address while in little endian architecture, the least significant byte is stored at lower address. The Intel x86 architecture is little endian and sun SPARC are big endian.More on Endianness
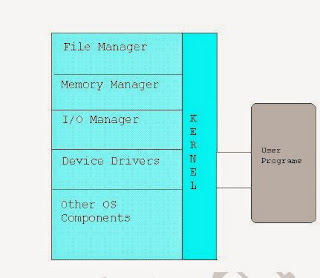
OS Kernel Architectures:The kernel of an operating system can be considered as the parliament house, which overpowers the whole country, in the same way every single event is controlled by the kernel in OS.An operating system itself consists of two parts: the kernel space (privileged mode) and the user space (unprivileged mode).
There are two main architectures of the kernels: monolithic & microkernel architecture
Monolithic Kernel architecture:The monolithic kernel acts as a single module.It runs every basic system service in kernel space.
The examples of monolithic kernel based OSs are Linux, Unix. Every time someone adds a new feature or fixes a bug, it means recompilation of the whole kernel.In monolithic kernel every logical part works in kernel mode in ring0
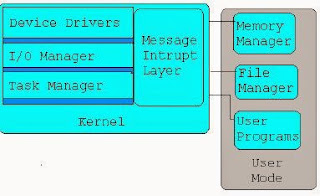
Microkernel architecture: In Microkernels, the kernel is broken down into separate processes, known as servers.Here only few modules(servers) work in kernel mode while most of important system managers work in the user space. All servers are kept separate and run in different address spaces.
The examples of monolithic kernel based OSs are Windows NT.if any error occurs in any module like in file manager or memory manager, then, it can safely be shutdown without affecting other kernel modules and system managers.
Security-wise,Monolithic Kernel OS(like Linux) are most stable than the Microkernel architecture based operating systems(like Windows NT) because in microkernel architecture, most of the operating system components work in user space and are unprotected, thus, an attacker can unplug any system component and can plug an altered Trojan module in its place to hide his activities and control the operating system to perform as desired. There is also a Myth that "Windows is more secure than Linux". Now i hope you must understand that Linux is more secure than Windows.
Memory Architecture: Memory is just a collection of bytes of temporary storage space that are numbered with addresses.it is used for storing both instructions to be executed and data.
A bit (short for "binary digit") is the smallest unit of measurement used to quantify computer data. It contains a single binary value of 0 or 1.The smallest unit of memory is a byte which is consist of 8 bits and a nibble consists of 4 bits. A byte can store one character in binary form. Other measuring units are kilobytes(KB) equal to 1024 bytes, megabytes(MB) is equal to 1024 KB and Gigabyte (GB) is equal to 1024 MB.
There are various memory devices like primary memory(RAM and ROM), cache memory, secondary memory devices(Like hard disk, CD ROMs, DVDs etc).
When we write programs, compiled it and executed, then Where the program is stored? The answer is in primary memory (RAM) Programs need to be in main( primary) memory in order to be executed.Programs not needed immediately may be kept in secondary memory until needed.
In digital representation various number systems are used like decimal, binary, octal hexadecimal. Many number system are useful in digital technology like computer.
Digital number system: it is composed of 10 numerals or symbols. These 10 symbols are 0,1,2,3,4,5,6,7,8,9
Binary number system: there are only two symbols i.e. 0 or 1 .This is base-2 system.
Octal number systems: It has base of eight, meaning that it has eight unique symbols: 0,1,2,3,4,5,6,7.
Hexadecimal number systems: It uses base 16. it has 16 possible digits symbols. it uses the digits 0 to 9 plus the letters A,B,C,D,E and F as the 16 digital symbols.
Now back to memory concept,Like a row of houses on a local street, each with its own address, memory can be thought of as a row of bytes, each with its own memory address. Each byte of memory can be accessed by its address.There are two types Intel processors : 32-bit and 64-bit.The 32-bit processors have 232 (or 4,294,967,296) possible addresses, while the 64-bit ones have 264 (1.84467441 × 1019) possible addresses.
Now we will discus the structure of the process memory space, its understanding will help in carrying out most of the attacks.It is always good to know the architecture of memory and the way memory is accessible to us as hacker.The memory allocation for every process is the headache of operating system.The memory that is assigned to program(executable formats) in Linux architecture can be divided Mainly into four segments:
.text(Text or Code Segment) :This section contains the executable instruction codes and is shared among every process running the same binary. This section usually has READ and EXECUTE permissions only.This section cannot be modified, so 'write' attribute is not associated with it. It means that the code section (.text) cannot be modified once the program is executing. Otherwise, any hacker can modify the code while executing the program and thus make the program to do what he wants or may crash it;therefore, it is not permitted.
.bss(Uninitialized Data Segment) :BSS stands for ‘Block Started by Symbol’. It holds un-initialized global and static variables. this segments is writable, also have a fixed size. Both global and static variables are able to persist because they are stored in their own memory segments
.data(Initialized Data Segments):Contains the initialized global and static variables and their values. It is usually the largest part of the executable. It usually has READ/WRITE permissions.But not execute for the sake of security.this section contains the data required by the executing code.
.rdata(Initialized Data Segments):The initiated & relocatable variables are saved in this section and has ‘read only’ attribute associated with it.
.bss can be divided into two parts:
1)Heap: Heap is also called dynamic memory section. The variables and objects, which are dynamically created, are
saved into this part of memory.The heap segment is a segment of memory a programmer can directly control. Blocks of memory in this segment can be allocated and used for whatever the programmer might need.
2) Stack: A stack is a storage device that stores information in such a manner that the item stored last is the first item received i.e. stack is a LIFO (Last Input First Output). This allows for the program to store information in memory and retrieve it easily. It also has many other purposes, is used to store all local variables and is used for passing arguments to the functions along with the return address of the instruction which is to be executed after the function call is over.
For assembly language programmer ,exploit writer and hacker it is important to understand the concept of stack.
Basic Instructions :
it allows allows the push and pop operations on word or double word data items.
push source
pop destination
Points to remember:
A “stack pointer” register tracks the top of the stack; it is adjusted each time a value is “pushed” onto the stack. The set of values pushed for one function call is termed a “stack frame”; A stack frame consists at minimum of a return address.
Each time a function is called, the address of where to return to and certain information about the caller’s environment are saved on the stack.
Each time a recursive function calls itself, a new stack frame is used, so one set of variables doesn’t interfere with the variables from another instance of the function.
The major difference between Heap and stack is, Heap grows downwards along with lower memory addresses to higher memory addresses. While the stack grows upward towards the heap from higher memory addresses to the lower memory addresses.
The implementation of stack and heap is very important to understand most worse kinds of attacks e.g. buffer overflow attack, off-by-one errors, etc. Special security features are implemented on the stack memory to thwart the attempts to overflow the memory. But don’t panic we will discus the ways to break in such security.
Now we will Putting the Pieces of Memory Together with a simple example :
int var = 10; // integer stored in data (initialized)
char * str; // string stored in bss (uninitialized)
int nothing; // integer stored in bss (uninitialized)
void funct1(int c){ // bracket starts function1 block
int i=c; // stored in the stack region
str = (char*) malloc (10 * sizeof (char)); // Reserves 10 //characters in the heap region
strncpy(str, "abcde", 5); //copies 5 characters "abcde" into str
} //end of function1
void main (){ //the required main function
funct1(1); //main calls function1 with an argument
} //end of the main function
This program does not do much and used to illustrate the usage of memory in a program
Always Remember, Good Hacker == Good Programmer.
if you like this post or have any question, please feel free to comment !
A programmer is one who only concerned with source code.A hacker is someone who is curious about how something(like computer) works.A hacker realizes that the compiled program is what actually gets executed out in the real world.The hacker wants to know the ins and outs, nuts and bolts of the entire thing.If you really want to be a hacker, you must want to understand the working guts of a computer.With a better understanding of how the CPU operates, a hacker can manipulate the programs that run on it.
A programmer writes the code,compiled it into an executable binary for the low level(x86 assumed) architecture. But what does this executable binary look like? It does not make sense to programmers but a hacker realizes that the compiled program is what actually gets executed out in the real world.With a better understanding of how the CPU operates, a hacker can manipulate the programs that run on it.
The CPU is is the heart of the system. it designed to do a couple of things:
Fetch an instruction from memory.
Execute the instruction.
There are two kind of processor architecture:
Big Endian
Little Endian
Little and big endian are two ways of storing multibyte data-types ( int, float, etc).Big endian stores data in such a way that most significant byte is stored at lower address while in little endian architecture, the least significant byte is stored at lower address. The Intel x86 architecture is little endian and sun SPARC are big endian.More on Endianness
OS Kernel Architectures:The kernel of an operating system can be considered as the parliament house, which overpowers the whole country, in the same way every single event is controlled by the kernel in OS.An operating system itself consists of two parts: the kernel space (privileged mode) and the user space (unprivileged mode).
There are two main architectures of the kernels: monolithic & microkernel architecture
Monolithic Kernel architecture:The monolithic kernel acts as a single module.It runs every basic system service in kernel space.
The examples of monolithic kernel based OSs are Linux, Unix. Every time someone adds a new feature or fixes a bug, it means recompilation of the whole kernel.In monolithic kernel every logical part works in kernel mode in ring0
Microkernel architecture: In Microkernels, the kernel is broken down into separate processes, known as servers.Here only few modules(servers) work in kernel mode while most of important system managers work in the user space. All servers are kept separate and run in different address spaces.
The examples of monolithic kernel based OSs are Windows NT.if any error occurs in any module like in file manager or memory manager, then, it can safely be shutdown without affecting other kernel modules and system managers.
Security-wise,Monolithic Kernel OS(like Linux) are most stable than the Microkernel architecture based operating systems(like Windows NT) because in microkernel architecture, most of the operating system components work in user space and are unprotected, thus, an attacker can unplug any system component and can plug an altered Trojan module in its place to hide his activities and control the operating system to perform as desired. There is also a Myth that "Windows is more secure than Linux". Now i hope you must understand that Linux is more secure than Windows.
Memory Architecture: Memory is just a collection of bytes of temporary storage space that are numbered with addresses.it is used for storing both instructions to be executed and data.
A bit (short for "binary digit") is the smallest unit of measurement used to quantify computer data. It contains a single binary value of 0 or 1.The smallest unit of memory is a byte which is consist of 8 bits and a nibble consists of 4 bits. A byte can store one character in binary form. Other measuring units are kilobytes(KB) equal to 1024 bytes, megabytes(MB) is equal to 1024 KB and Gigabyte (GB) is equal to 1024 MB.
There are various memory devices like primary memory(RAM and ROM), cache memory, secondary memory devices(Like hard disk, CD ROMs, DVDs etc).
When we write programs, compiled it and executed, then Where the program is stored? The answer is in primary memory (RAM) Programs need to be in main( primary) memory in order to be executed.Programs not needed immediately may be kept in secondary memory until needed.
In digital representation various number systems are used like decimal, binary, octal hexadecimal. Many number system are useful in digital technology like computer.
Digital number system: it is composed of 10 numerals or symbols. These 10 symbols are 0,1,2,3,4,5,6,7,8,9
Binary number system: there are only two symbols i.e. 0 or 1 .This is base-2 system.
Octal number systems: It has base of eight, meaning that it has eight unique symbols: 0,1,2,3,4,5,6,7.
Hexadecimal number systems: It uses base 16. it has 16 possible digits symbols. it uses the digits 0 to 9 plus the letters A,B,C,D,E and F as the 16 digital symbols.
Now back to memory concept,Like a row of houses on a local street, each with its own address, memory can be thought of as a row of bytes, each with its own memory address. Each byte of memory can be accessed by its address.There are two types Intel processors : 32-bit and 64-bit.The 32-bit processors have 232 (or 4,294,967,296) possible addresses, while the 64-bit ones have 264 (1.84467441 × 1019) possible addresses.
Now we will discus the structure of the process memory space, its understanding will help in carrying out most of the attacks.It is always good to know the architecture of memory and the way memory is accessible to us as hacker.The memory allocation for every process is the headache of operating system.The memory that is assigned to program(executable formats) in Linux architecture can be divided Mainly into four segments:
.text(Text or Code Segment) :This section contains the executable instruction codes and is shared among every process running the same binary. This section usually has READ and EXECUTE permissions only.This section cannot be modified, so 'write' attribute is not associated with it. It means that the code section (.text) cannot be modified once the program is executing. Otherwise, any hacker can modify the code while executing the program and thus make the program to do what he wants or may crash it;therefore, it is not permitted.
.bss(Uninitialized Data Segment) :BSS stands for ‘Block Started by Symbol’. It holds un-initialized global and static variables. this segments is writable, also have a fixed size. Both global and static variables are able to persist because they are stored in their own memory segments
.data(Initialized Data Segments):Contains the initialized global and static variables and their values. It is usually the largest part of the executable. It usually has READ/WRITE permissions.But not execute for the sake of security.this section contains the data required by the executing code.
.rdata(Initialized Data Segments):The initiated & relocatable variables are saved in this section and has ‘read only’ attribute associated with it.
.bss can be divided into two parts:
1)Heap: Heap is also called dynamic memory section. The variables and objects, which are dynamically created, are
saved into this part of memory.The heap segment is a segment of memory a programmer can directly control. Blocks of memory in this segment can be allocated and used for whatever the programmer might need.
2) Stack: A stack is a storage device that stores information in such a manner that the item stored last is the first item received i.e. stack is a LIFO (Last Input First Output). This allows for the program to store information in memory and retrieve it easily. It also has many other purposes, is used to store all local variables and is used for passing arguments to the functions along with the return address of the instruction which is to be executed after the function call is over.
For assembly language programmer ,exploit writer and hacker it is important to understand the concept of stack.
Basic Instructions :
it allows allows the push and pop operations on word or double word data items.
push source
pop destination
Points to remember:
A “stack pointer” register tracks the top of the stack; it is adjusted each time a value is “pushed” onto the stack. The set of values pushed for one function call is termed a “stack frame”; A stack frame consists at minimum of a return address.
Each time a function is called, the address of where to return to and certain information about the caller’s environment are saved on the stack.
Each time a recursive function calls itself, a new stack frame is used, so one set of variables doesn’t interfere with the variables from another instance of the function.
The major difference between Heap and stack is, Heap grows downwards along with lower memory addresses to higher memory addresses. While the stack grows upward towards the heap from higher memory addresses to the lower memory addresses.
The implementation of stack and heap is very important to understand most worse kinds of attacks e.g. buffer overflow attack, off-by-one errors, etc. Special security features are implemented on the stack memory to thwart the attempts to overflow the memory. But don’t panic we will discus the ways to break in such security.
Now we will Putting the Pieces of Memory Together with a simple example :
int var = 10; // integer stored in data (initialized)
char * str; // string stored in bss (uninitialized)
int nothing; // integer stored in bss (uninitialized)
void funct1(int c){ // bracket starts function1 block
int i=c; // stored in the stack region
str = (char*) malloc (10 * sizeof (char)); // Reserves 10 //characters in the heap region
strncpy(str, "abcde", 5); //copies 5 characters "abcde" into str
} //end of function1
void main (){ //the required main function
funct1(1); //main calls function1 with an argument
} //end of the main function
This program does not do much and used to illustrate the usage of memory in a program
Always Remember, Good Hacker == Good Programmer.
if you like this post or have any question, please feel free to comment !
We are a full-service digital agency building brands across all digital niches, including Website & App Development, DevOps, and Media Strategy.
ReplyDeleteweb development
hire a web developer