What is Assembly language?
As i am already discussed, There are three types of computer programming languages:Machine Language,Assembly Language,High-Level Language.
Machine language:To instruct a computer to do something, the instructions must be written in its language.A computer understand set of instructions written in machine language i.e binary language.Binary means that there is a code of either 0 or 1 also known as OFF or ON.
Assembly language: This is the same as machine language, except the command numbers been replaced by commands like jmp,mov, push etc. which are easier to memorize.
High-level language: A program written in a high-level language is much more readable.Program written in a high-level language can be translated into many machine language and therefore can run on any computer for which there exists an appropriate translator. A compiler converts a high-level language into machine language.
Assembly for hackers and security researchers:
Many people(Programmers and hackers) thinks that high level language like Java, c/c++ are more useful than the Assembly language. But this is the wrong myth among them.Because assembly language allows you to do things you can't do in other programming languages. Without assembly language you will not be able to find the 0day against software , because debugger only output in asm code.In reality you don't need to be able to code in assembly, you need to be able to analyses malware and exploits and that is something else completely from coding for functionality.Actually you don't need to be coder but you should able to read it, understand it. Also if you want to know how computer internal works then best way to learn asm.To be able to truly understand the way that a program can exploit a system, you are going to have to understand that system on a lower level.If you wish to write exploits you need assembly knowledge, there is plenty of great shellcode around but to get your exploit to the point where you can execute the shellcode you need assembly knowledge. Metasploit is a great resource for the shellcode and to shovel in your exploit, but to understand the inner executions and workings of any binary you need to understand assembly.
Remember for hacker, assembly language is must. A hacker that hasn’t mastered Assembly language is not a hacker because nothing really moves without it.
Who Needs to Learn Assembly language :
-> Malware Analysts.
-> Code Exploit Writers.
-> Reverse Code Engineers.
-> Shellcoders.
-> Software Vulnerability Analysts.
-> Bug Hunters.
-> Virus Writers.
Learn Assembly: Assembly language is probably the most important things one needs to master if he/she desire to enter the world of hacking. It is a little difficult language as compared to C/C++ or python. Suppose you have want to find vulnerability in a software. As is obvious, You will not have the source code. this is where assembly comes in action. The application of assembly language is in finding security holes or bug without the source code(Written in C/C++). Assembly knowledge will help at almost every stage of exploitation. Assembly language programming is mandatory for developing your own exploits.The assembly language is also used for malware , rootkits, viruses writing, etc.Another application of assembly is in writing shellcoding. However,a decent understanding of x86 assembly, C, and knowledge of the Linux and Windows operating systems is required for writing shellcode.
To write assembly language for any processor , you must know low-level details of the processor architecture you are writing. Assembly language is depend on machine architecture.Here on this blog Programming : Ethical Hacker way , you'll find complete tutorials for learning assembly in hacker way.
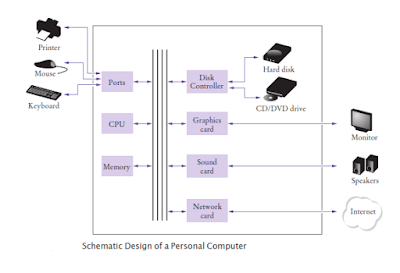
Computer architecture: As we already discussed, To write assembly language for any processor , you must know low-level details of the processor architecture you are writing. We will look at a personal computer. Larger computers have faster, larger, or more powerful components, but they have fundamentally the same design.We can divides the computer up into two main parts - the CPU (for Central Processing Unit) and the memory. This architecture is used in all modern computers,including personal computers, supercomputers, mainframes, and even cell phones.
1. Memory: There are two kinds of storage. Primary storage is made from memory chips: electronic circuits that can store data, provided they are supplied with electric power. Secondary storage, usually a hard disk,provides less expensive storage that persists without electricity. Programs and data are typically stored on the hard disk and loaded into memory when the program starts. The program then updates the data in memory and writes the modified data back to the hard disk. Computer memory is a numbered sequence of fixed-size storage locations. The number attached to each storage location is called it’s address. The size of a single storage location is called a byte. On x86 processors,a byte is a number between 0 and 255.
2. CPU: Simply storing data doesn't do much help - you need to be able to access, manipulate, and move it.That’s where the CPU comes in.At the heart of the computer lies the central processing unit (CPU). It consists of a single chip, or a small number of chips. The CPU performs program control and data processing. That is, the CPU locates and executes the program instructions; it carries out arithmetic operations such as addition, subtraction, multiplication, and division; it fetches data from external memory or devices and stores data back.
The schematic overview of the architecture of a personal computer:
Program instructions and data (such as text, numbers, audio, or video) are stored on the hard disk, on an optical disk such as a DVD, or elsewhere on the network. When a program is started, it is brought into memory, where the CPU can read it. The CPU reads the program one instruction at a time. As directed by these instructions, the CPU reads data, modifies it, and stores it. Some program instructions will cause the CPU to place dots on the display screen or printer or to vibrate the speaker. As these actions happen many times over and at great speed, the human user perceives images and sound. Some program instructions read user input from the keyboard or mouse. After understanding basic assembly language, now we will start writing assembly programs.
Tools and platform used for Assembly language: Before we starts writing assembly programs, let me tell you which tools and platform we are going to use.
1. Development Platform:-
Linux: we will use Kali-linux which is a Debian-derived Linux distribution designed for digital forensics and penetration testing.
More Detail : http://en.wikipedia.org/wiki/Kali_Linux
You can download it from here: https://www.kali.org/
2. Assembler :- GAS (The GNU Assembler) : The GNU Assembler is used to convert ARM assembly language source code into binary object files.
You don't need to download it. It is installed by default in Kali-linux.
3. Linker:- ld : it is a tool used for linking GNU linker (or GNU ld) is the GNU Project's implementation of the Unix command ld.
It is also installed by default in Kali-linux.
4.Debugger:- GDB : GDB, the GNU Project debugger, allows you to see what is going on 'inside' another program while it executes -- or what another program was doing at the moment it crashed.
GDB can do four main kinds of things (plus other things in support of these) to help you catch bugs in the
act:
1.Start your program, specifying anything that might affect its behavior.
2.Make your program stop on specified conditions.
3.Examine what has happened, when your program has stopped.
4.Change things in your program, so you can experiment with correcting the effects of one bug and go on to learn about another.
It is also available in kali-linux.
Reference: http://programmingethicalhackerway.blogspot.com/2015/07/introduction-to-programming-why-hacker.html
If you like this post or have any question, please feel free to comment!
As i am already discussed, There are three types of computer programming languages:Machine Language,Assembly Language,High-Level Language.
Machine language:To instruct a computer to do something, the instructions must be written in its language.A computer understand set of instructions written in machine language i.e binary language.Binary means that there is a code of either 0 or 1 also known as OFF or ON.
Assembly language: This is the same as machine language, except the command numbers been replaced by commands like jmp,mov, push etc. which are easier to memorize.
High-level language: A program written in a high-level language is much more readable.Program written in a high-level language can be translated into many machine language and therefore can run on any computer for which there exists an appropriate translator. A compiler converts a high-level language into machine language.
Assembly for hackers and security researchers:
Many people(Programmers and hackers) thinks that high level language like Java, c/c++ are more useful than the Assembly language. But this is the wrong myth among them.Because assembly language allows you to do things you can't do in other programming languages. Without assembly language you will not be able to find the 0day against software , because debugger only output in asm code.In reality you don't need to be able to code in assembly, you need to be able to analyses malware and exploits and that is something else completely from coding for functionality.Actually you don't need to be coder but you should able to read it, understand it. Also if you want to know how computer internal works then best way to learn asm.To be able to truly understand the way that a program can exploit a system, you are going to have to understand that system on a lower level.If you wish to write exploits you need assembly knowledge, there is plenty of great shellcode around but to get your exploit to the point where you can execute the shellcode you need assembly knowledge. Metasploit is a great resource for the shellcode and to shovel in your exploit, but to understand the inner executions and workings of any binary you need to understand assembly.
Remember for hacker, assembly language is must. A hacker that hasn’t mastered Assembly language is not a hacker because nothing really moves without it.
Who Needs to Learn Assembly language :
-> Malware Analysts.
-> Code Exploit Writers.
-> Reverse Code Engineers.
-> Shellcoders.
-> Software Vulnerability Analysts.
-> Bug Hunters.
-> Virus Writers.
Learn Assembly: Assembly language is probably the most important things one needs to master if he/she desire to enter the world of hacking. It is a little difficult language as compared to C/C++ or python. Suppose you have want to find vulnerability in a software. As is obvious, You will not have the source code. this is where assembly comes in action. The application of assembly language is in finding security holes or bug without the source code(Written in C/C++). Assembly knowledge will help at almost every stage of exploitation. Assembly language programming is mandatory for developing your own exploits.The assembly language is also used for malware , rootkits, viruses writing, etc.Another application of assembly is in writing shellcoding. However,a decent understanding of x86 assembly, C, and knowledge of the Linux and Windows operating systems is required for writing shellcode.
To write assembly language for any processor , you must know low-level details of the processor architecture you are writing. Assembly language is depend on machine architecture.Here on this blog Programming : Ethical Hacker way , you'll find complete tutorials for learning assembly in hacker way.
Computer architecture: As we already discussed, To write assembly language for any processor , you must know low-level details of the processor architecture you are writing. We will look at a personal computer. Larger computers have faster, larger, or more powerful components, but they have fundamentally the same design.We can divides the computer up into two main parts - the CPU (for Central Processing Unit) and the memory. This architecture is used in all modern computers,including personal computers, supercomputers, mainframes, and even cell phones.
1. Memory: There are two kinds of storage. Primary storage is made from memory chips: electronic circuits that can store data, provided they are supplied with electric power. Secondary storage, usually a hard disk,provides less expensive storage that persists without electricity. Programs and data are typically stored on the hard disk and loaded into memory when the program starts. The program then updates the data in memory and writes the modified data back to the hard disk. Computer memory is a numbered sequence of fixed-size storage locations. The number attached to each storage location is called it’s address. The size of a single storage location is called a byte. On x86 processors,a byte is a number between 0 and 255.
2. CPU: Simply storing data doesn't do much help - you need to be able to access, manipulate, and move it.That’s where the CPU comes in.At the heart of the computer lies the central processing unit (CPU). It consists of a single chip, or a small number of chips. The CPU performs program control and data processing. That is, the CPU locates and executes the program instructions; it carries out arithmetic operations such as addition, subtraction, multiplication, and division; it fetches data from external memory or devices and stores data back.
The schematic overview of the architecture of a personal computer:
Program instructions and data (such as text, numbers, audio, or video) are stored on the hard disk, on an optical disk such as a DVD, or elsewhere on the network. When a program is started, it is brought into memory, where the CPU can read it. The CPU reads the program one instruction at a time. As directed by these instructions, the CPU reads data, modifies it, and stores it. Some program instructions will cause the CPU to place dots on the display screen or printer or to vibrate the speaker. As these actions happen many times over and at great speed, the human user perceives images and sound. Some program instructions read user input from the keyboard or mouse. After understanding basic assembly language, now we will start writing assembly programs.
Tools and platform used for Assembly language: Before we starts writing assembly programs, let me tell you which tools and platform we are going to use.
1. Development Platform:-
Linux: we will use Kali-linux which is a Debian-derived Linux distribution designed for digital forensics and penetration testing.
More Detail : http://en.wikipedia.org/wiki/Kali_Linux
You can download it from here: https://www.kali.org/
2. Assembler :- GAS (The GNU Assembler) : The GNU Assembler is used to convert ARM assembly language source code into binary object files.
You don't need to download it. It is installed by default in Kali-linux.
3. Linker:- ld : it is a tool used for linking GNU linker (or GNU ld) is the GNU Project's implementation of the Unix command ld.
It is also installed by default in Kali-linux.
4.Debugger:- GDB : GDB, the GNU Project debugger, allows you to see what is going on 'inside' another program while it executes -- or what another program was doing at the moment it crashed.
GDB can do four main kinds of things (plus other things in support of these) to help you catch bugs in the
act:
1.Start your program, specifying anything that might affect its behavior.
2.Make your program stop on specified conditions.
3.Examine what has happened, when your program has stopped.
4.Change things in your program, so you can experiment with correcting the effects of one bug and go on to learn about another.
It is also available in kali-linux.
Reference: http://programmingethicalhackerway.blogspot.com/2015/07/introduction-to-programming-why-hacker.html
If you like this post or have any question, please feel free to comment!
NIce Blog For Linux Learn Python the Hard Way
ReplyDeleteSaurav
ReplyDeleteNice
ReplyDeleteThis information is really awesome thanks for sharing most valuable information.
ReplyDeletePoint cloud to 3D Model Reading
Scan to BIM in California
3d Laser Scanning Services in Georgia
Reverse Engineering Services in California